
For our Expert Roundtable dedicated to the future ofIAM (Identity and Access Management), we welcomed four speakers: Gwendoline DENISSE (LastPass), Thomas Varillon (Neverhack), Karim LAMOURI (Hackers Without Borders) and Benoît MOREAU (KNDS France). Guided by Yasmine DOUADI, our experts analyzed the challenges of IAM in the face of the rise ofartificial intelligence and to new malicious practices.
Internal data theft: an underestimated risk
We first presented the results of a LinkedIn survey carried out with our community on the question: “Would an employee threatened with dismissal go so far as to steal sensitive company data? ”
Among 1,252 voters, 53% answered yes, 21% no and 26% “it depends”.
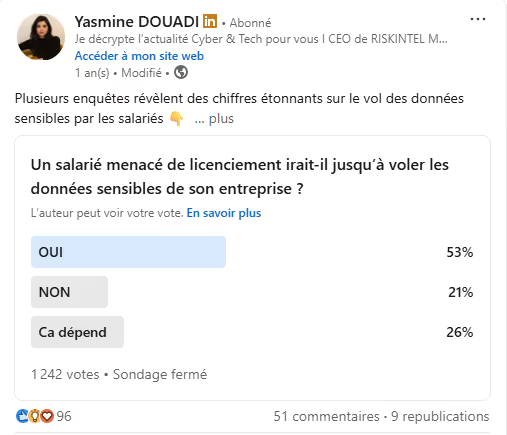
“These numbers are frightening!“comments Benoît MOREAU.
Gwendoline DENISSE adds:”It would be interesting to know if this information is being retrieved for harm or for personal benefit.“
Karim LAMOURI nuances:”Employees who have access to certain data are not always aware of their sensitivity.“
These results echo a study 2008 Cyber-Ark, which revealed that 88% of IT administrators would be ready to steal sensitive data in the event of dismissal. The period between the announcement and the effect of the dismissal is critical: it can allow an employee to retrieve strategic information.
Protecting data with IAM
To prevent this type of risk, businesses must adopt a proactive identity and access management. Privilege automation makes it possible to cut off access to information as soon as a role changes or an employee leaves the organization.
Other measures complement this strategy:
“The employee can always take photos of the data, so it is very difficult to protect it completely” underlines Karim Lamouri.
Extraordinary measures, such as a ban on physical access to the workstation, may apply when critical information is at stake. The processes of the type Red Button allow access to be cut off in a few hours, or even immediately.
Shadow IT: an invisible danger
The Shadow IT refers to systems and applications implemented by employees without control of RSSI. For example, an employee can install an application to respond to a customer, but it escapes the supervision of the company.
This practice increases the vulnerable entry points, and makes network security more complex. The permeability between personal and professional passwords facilitates attacks.
Gwendoline DENISSE illustrates the risk with two examples:
- LinkedIn 2012 : a remote employee hosted a personal blog on his professional workstation. A flaw exploited by hackers allowed access to the internal network.
- dropbox : a few months later, a Password Spraying exploited password reuse between LinkedIn and Dropbox.
“Shadow IT is difficult to quantify and even more difficult to control” recalls Gwendoline Denisse
Artificial intelligence as a threat amplifier
IAM guarantees the identity of the person who logs in, protecting systems against password theft, whether carried out via phishing or by AI.
Les Deepfakes, images and audio generated by AI, represent a new and sophisticated threat. In the case Arup, cybercriminals deceived a Hong Kong financier by pretending to be the CFO and other executives, causing A transfer of $25 million.
AI does not create new attacks but it amplifies them,” explains Thomas Varillon.
Employee awareness is becoming essential to guard against these attacks.
The MFA: the cornerstone of IAM
Benoît MOREAU reminds us:”The length or complexity of a password no longer protects. Password protection is dead.“
However, it is still essential to Do not reuse your passwords. The Multi-Factor Authentication (MFA), combined with password managers like LastPass, is now a must.
According to a LastPass 2023 study, 57% of businesses use the MFA. But the number alone is not revealing: you have to check What accesses are protected, and that the device is properly installed and monitored.
Boundaries and adoption
Some businesses are hesitant to deploy MFA due to the cost And of the Employee fatigue, who can click “yes” without checking. Karim LAMOURI adds:”Employees don't always want to use their personal phone to receive a business code.“
Centralized identity platforms, such as France Connect or “Connect with Google”, simplify access to services, but require MFA mandatory to avoid the risk associated with a unique password.
Biometrics and password alternatives
La biometrics is hard to usurp, but it's not infallible. Regulations on the collection and storage of biometric data vary by country.
“I don't want my biometric data to be used for this purpose“, affirms Karim LAMOURI.
Solutions such as Passkeys are also vulnerable, as shown by a recent flaw in YubiKeys, making it possible to steal cryptographic keys via the electrical analysis of the microcontroller.
Regulations and IAM
Several European regulations reinforce the authentication and monitoring of identities:
- CRA : cyber-resilience
- NIS 2 : harmonization of cybersecurity practices
- DORA : strengthening the resilience of financial organizations (effective January 2025)
These texts require companies to strengthen the system and access protection, and to implement solutions like MFA and the Least Privilege.
Thus, passwords alone are no longer enough: according to Verizon 2021, 81% of data breaches would be linked to this weakness. The reuse of passwords remains a key factor in cyberattacks.
THEIAM, the MFA, the privilege management And the user awareness are now the main defenses against data theft, shadow IT, and the exploitation of AI by malicious actors.
.jpg)
To find all our other items, see the complete library of our cybersecurity articles.
As for our programs, from which this article is based, you can check out our YouTube channel.









.avif)